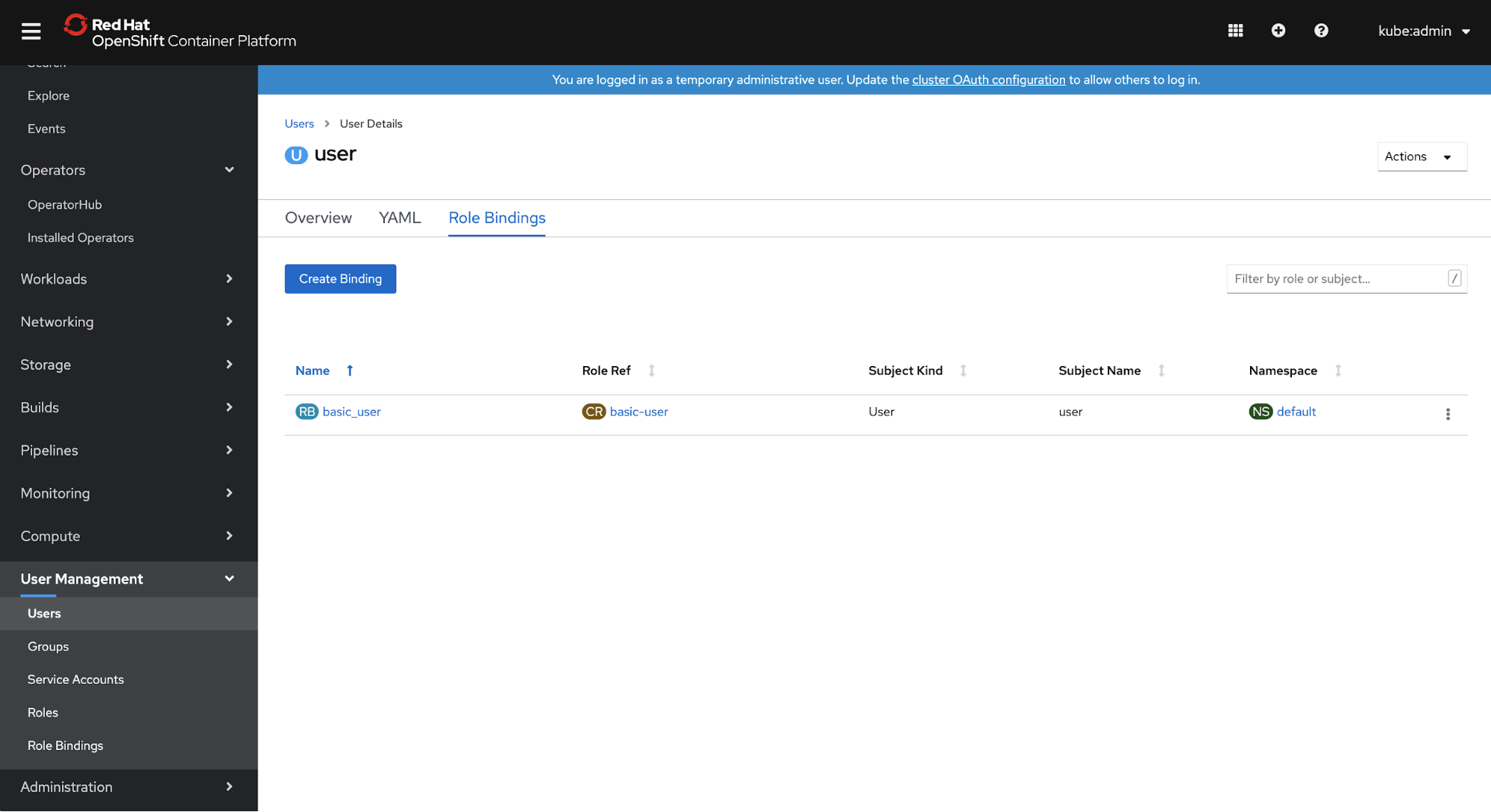
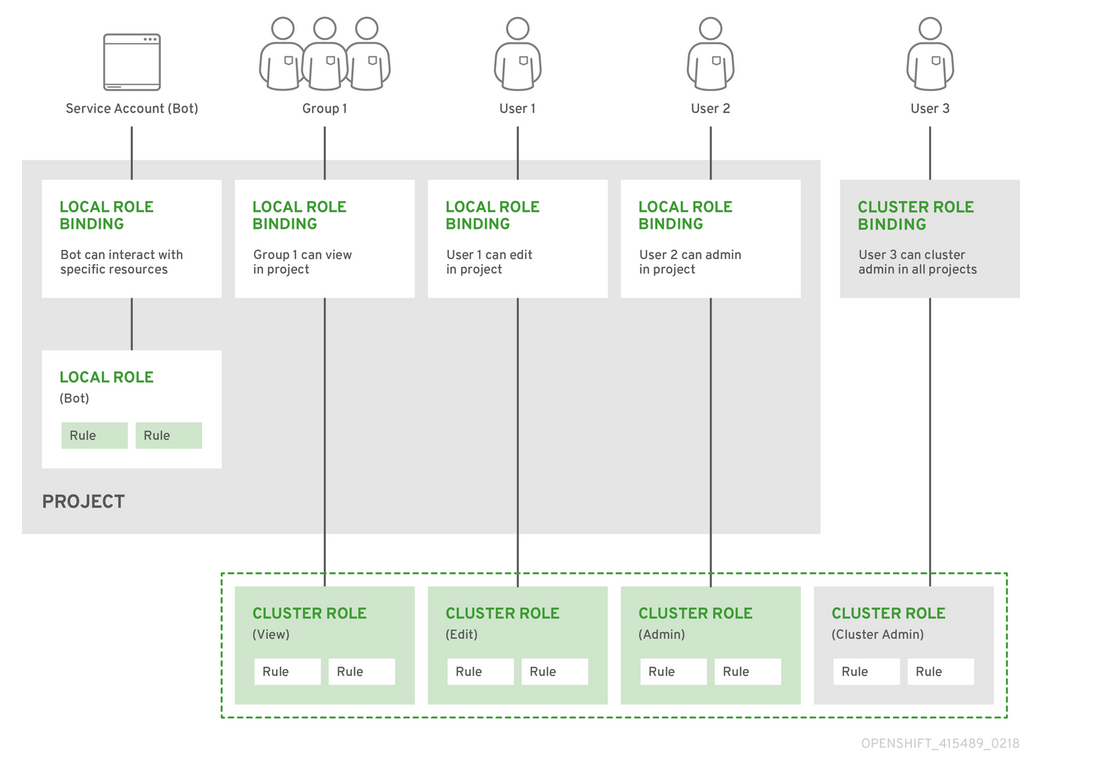
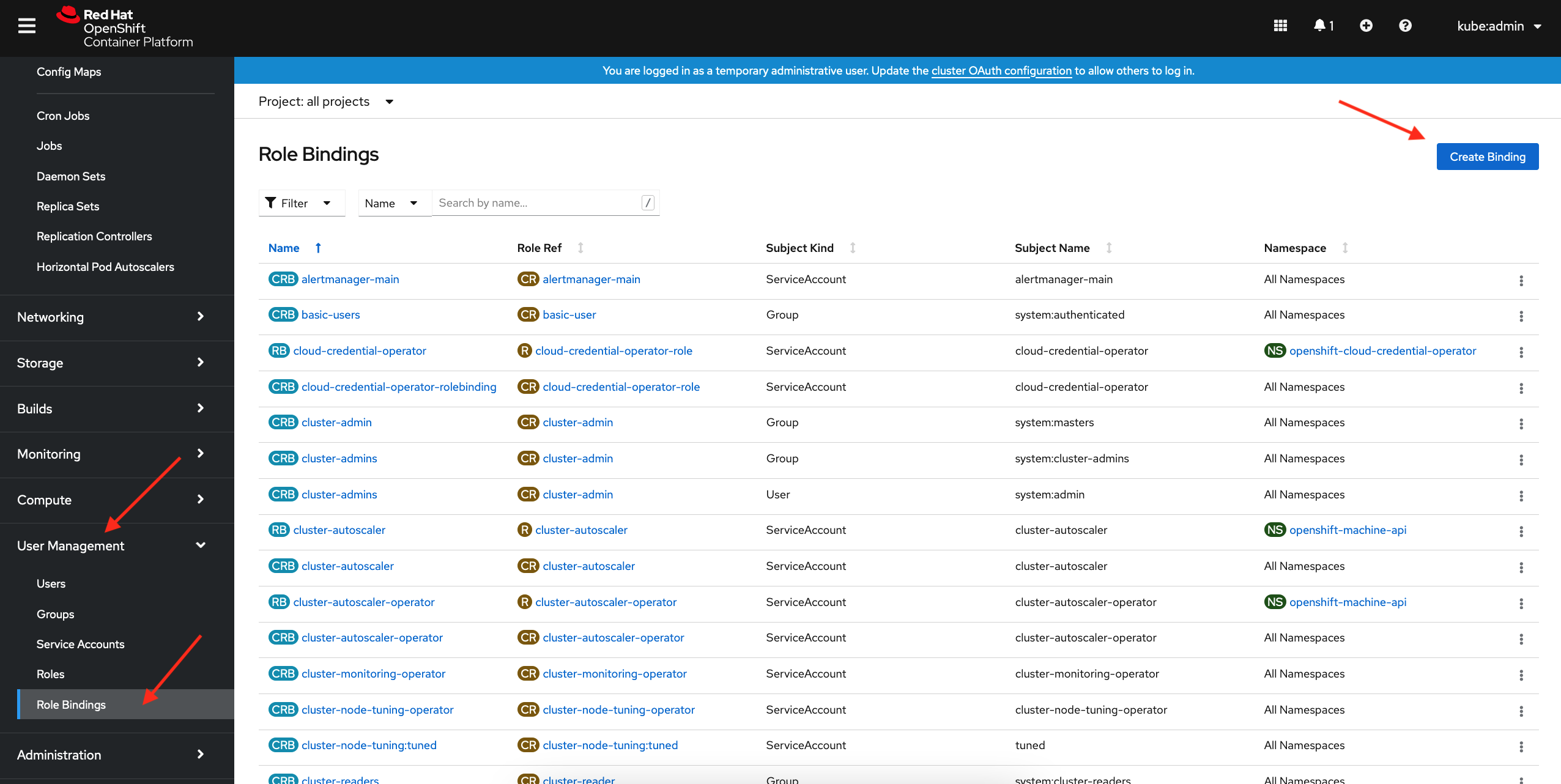
Chapter 8. Using RBAC to define and apply permissions OpenShift Container Platform 4.14 | Red Hat Customer Portal
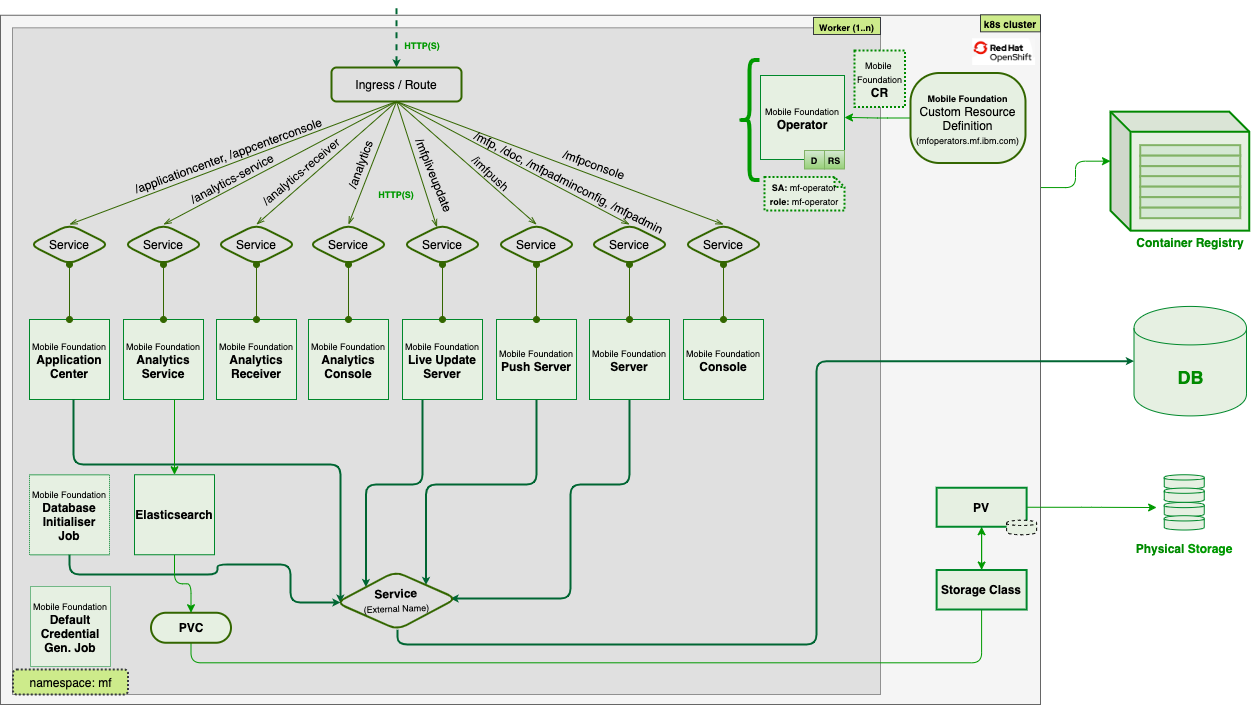
Deploy Mobile Foundation to an existing Red Hat OpenShift Container Platform - IBM Mobile Foundation Developer Center
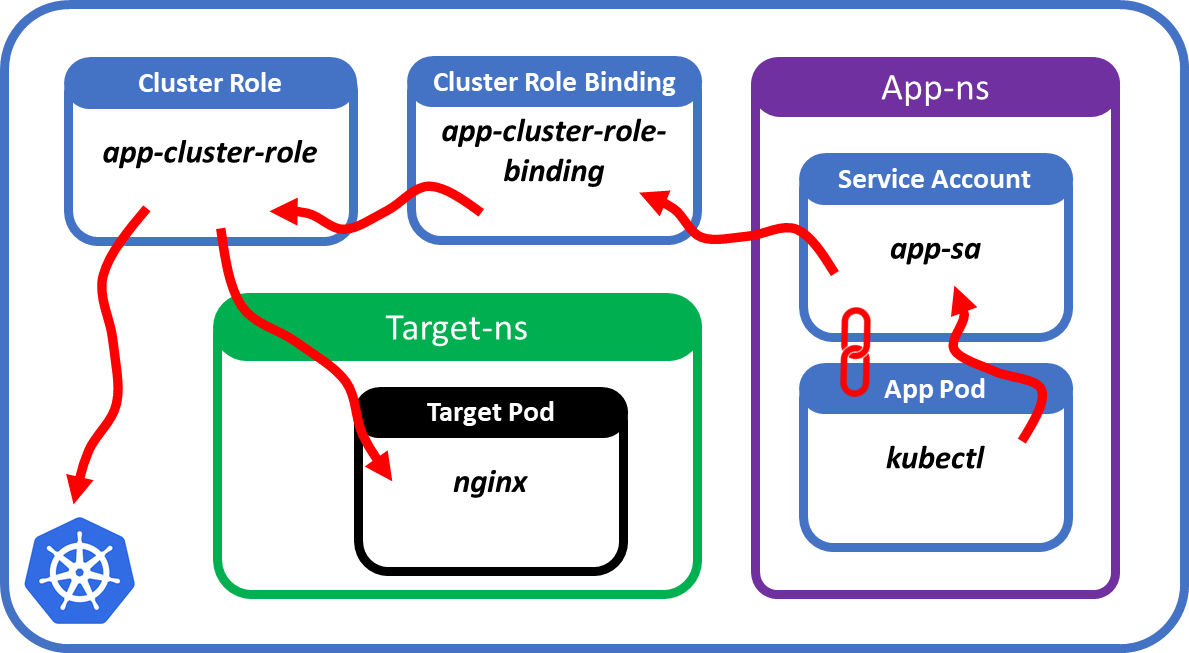
Unleashing the Power of Kubernetes: Deploying Containers with Cluster Resource Access for KCP-Edge | by Franco Stellari | Feb, 2023 | ITNEXT | ITNEXT

Red Hat OpenShift on X: "OpenShift 4.3: Spoofing a User https://t.co/zgVZCKA4nv - Improved troubleshooting - Live UX testing - “see what your users see” https://t.co/zvi7s9vpFs" / X


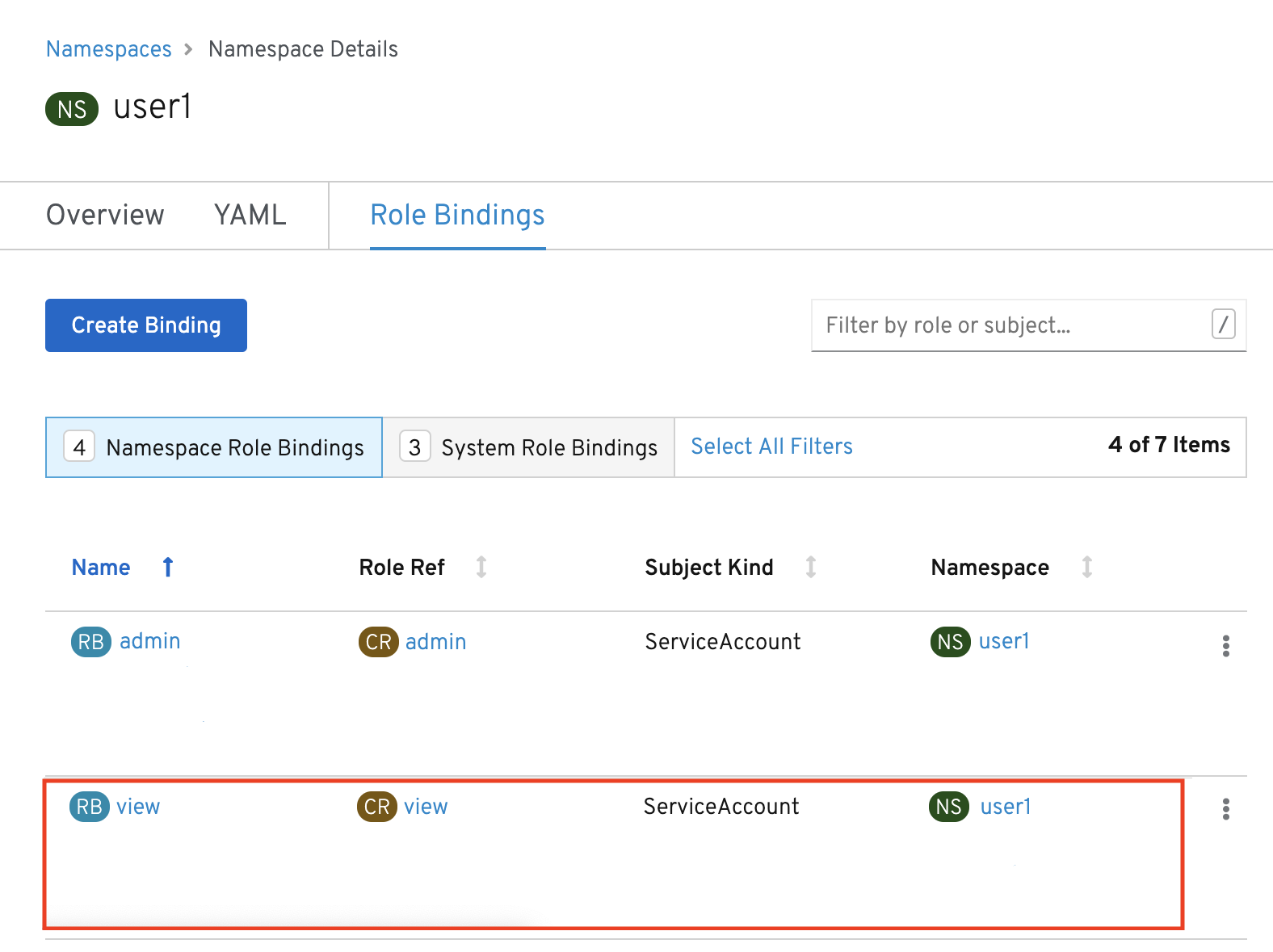
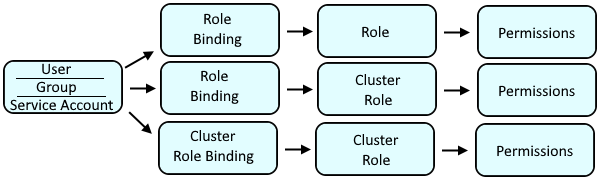
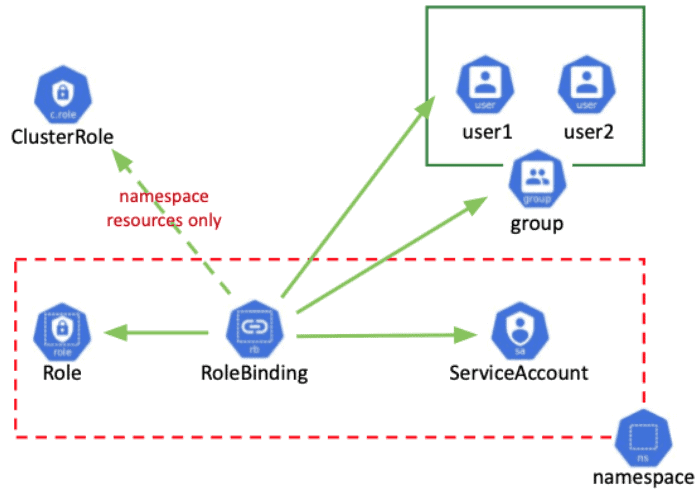


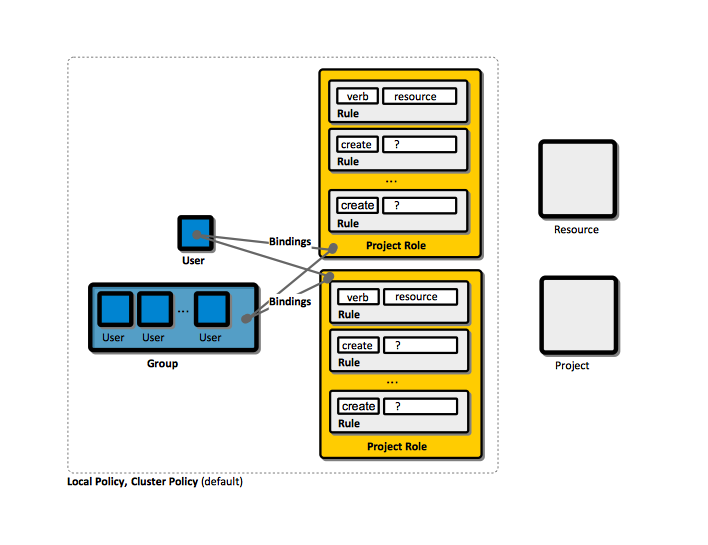
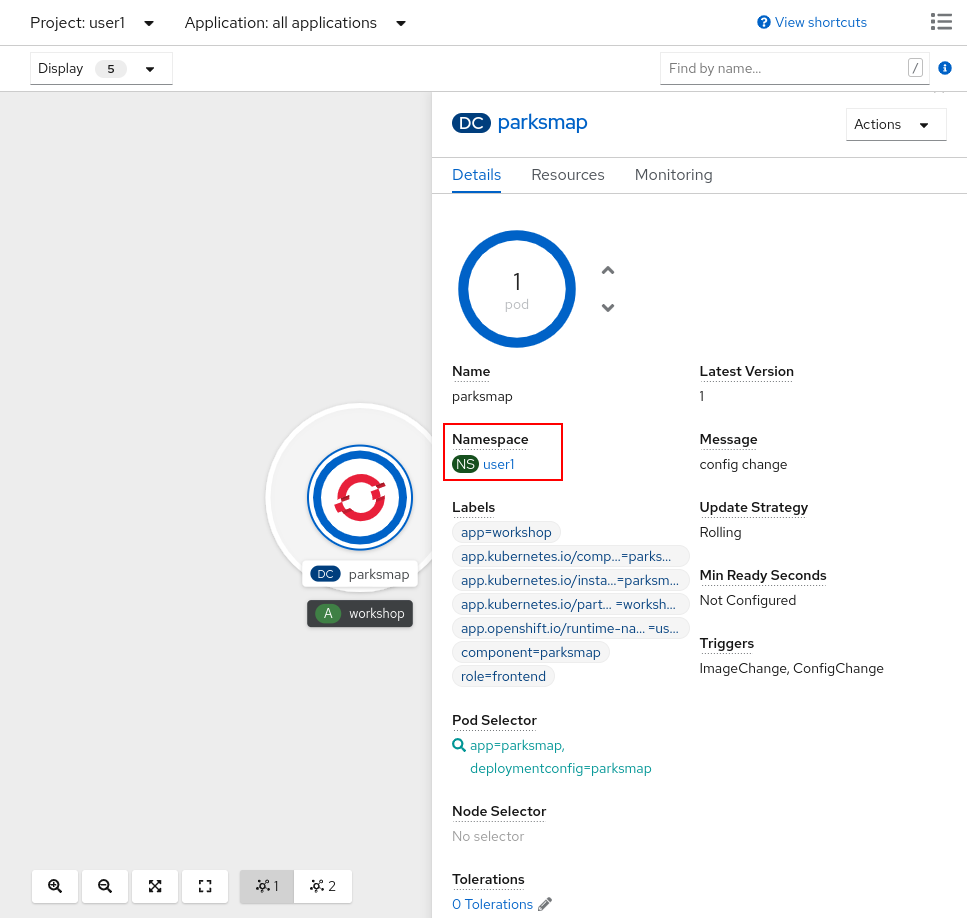
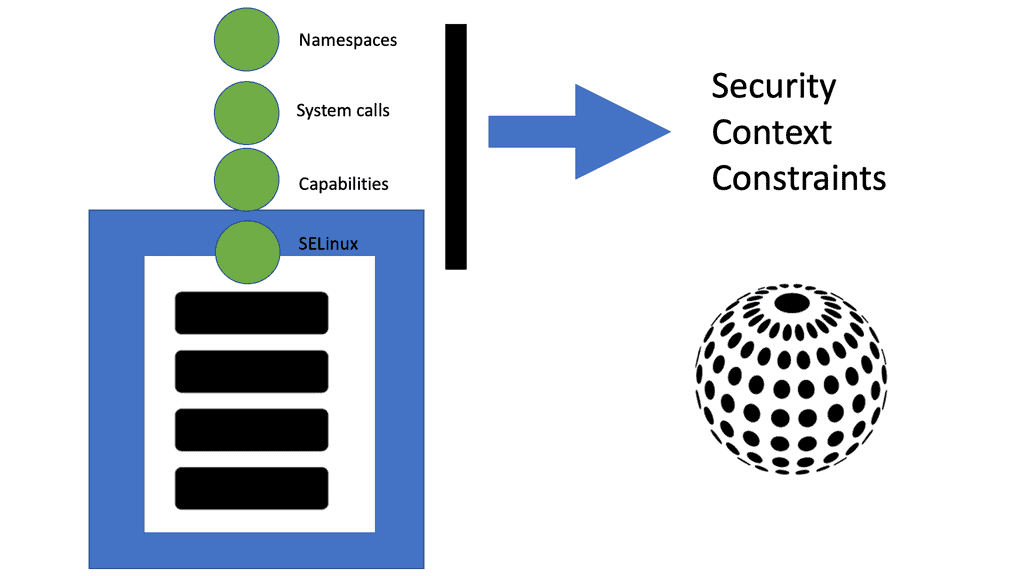
![4. Authorization - Kubernetes Security [Book] 4. Authorization - Kubernetes Security [Book]](https://www.oreilly.com/api/v2/epubs/9781492039075/files/assets/kuse_0401.png)
![Recap] Day 3: Authentication and Authorization | Openshift Recap] Day 3: Authentication and Authorization | Openshift](https://k21academy.com/wp-content/uploads/2021/11/rbac-1.png)